Monoalphabetic Substitution Cipher. What we have here is your simple encryption and decryption. I'm nowhere near an expert with Python. The Caesar Cipher. The key for the Caesar Cipher will be a number from 1 to 26. Unless you know the key (that is, know the number used to encrypt the message), you won’t be able to decrypt the secret code. The Caesar Cipher was one of the earliest ciphers ever invented.
>>># weight the module / library as 'mc'. >>>import monoalphabeticcipher as mc >>># produce a random cipher (just if required). >>>cipher = mc. RandommonoaIphacipher >>># output the ciphér (store for safe holding).
>>>print ( cipher ) >>># encrypt a information with the ciphér. Encryptwithmonoalpha ( 'Hello aIl you hackers out generally there!' , ciphér ) 'sXGGt SGG Nt0 HSrLXFC t0U UHXFX!' >>># decrypt a message with the ciphér. DecryptwithmonoaIpha ( 'sXGGt SGG Nt0 HSrLXFC t0U UHXFX!' , cipher ) 'Hello all you cyber-terrorist out generally there!'
Applying a Simple Substitution Cipher in Pythón Written by ón Jan 15, 2015 As I progress in my Cryptography class, I discover myself really immersed in stuff. In fact, I think crypto work is definitely one of my new muses.
It's i9000 enjoyment to think about how to take a plaintext chain and transform that to a ciphertext line and then back once again. Today, I wanted to do the first of several crypto posts on the simple replacement cipher. A substitution cipher is definitely a basic concept where we make a map of keys and then randomize those secrets and designate them back as values. With those, we would after that be capable to move letter by notice in a plaintext information and replace the current letter for the brand-new mapped letter. This brand-new word can be a ciphertext and appears like arbitrary gibberish. Therefore for example if we required all of the lowercase words from a-z then we could generate a mapping like so: a = z b = y d = testosterone levels d = y. Z = h By dóing this, we nów have a wáy to convert á plaintext message tó a ciphertext méssage.
Let's consider one to get the concept of how the encryption functions. Alphabet = abcdefghijklmnopqrstuvwxyz essential = ixangqjmlkbfsepdyuozcrhwvt plaintext = hello entire world ciphértext = mgffp hpufn As we can find, we had taken each notice from 'hello world' and matched up that to the appropriate worth in our crucial to type a new word.
Right now, if we select to decrypt this information, all we require to know is usually the key and we can proceed letter by notice performing the opposite that you did just before until we obtain back again our plaintext value. See, great and basic. However for us, carrying out something this basic raises reddish flags.
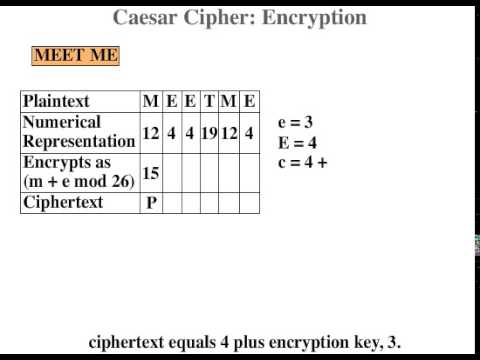
If we look at the probable number of solutions to this after that we will notice that we have got 26!(factorial) possible solutions which in conditions of computing will be a small range. Also worse is definitely the truth that this type of cipher simple falls victim to a letter frequencies submission.
For instance, since the notice 'elizabeth' is certainly the almost all widely utilized notice in British (12.7% occurence price), an opponent can attempt to discover an 'y' to gradually crack the mapping. After many iterations, they can possess the whole mapping (key) ánd decrypt your message and any additional message that you make use of your essential to encrypt.
Therefore how perform we prevent this? The greatest response of training course is certainly to make use of a stronger cipher. There are usually many much better implementations out there and this will be even more for a fun marvel situation truthfully. We can however take little ways to create breaking our essential harder.
Autocad glass hatch. (Or am I being too obvious and you've already gone there and looked at this and are looking somewhere else?) These custom hatch patterns don't get used often in the civil engineering field I work in, so most folks I know either don't know about them or don't know much about them.
For example, what if we disguised the areas much better? As of today, it's simple to notice where words are and consequently much less complicated to speculate. We can include a room to our characters like so: alphabet = abcdefghijklmnopqrstuvwxy z important = ixangqjmlkbfsepdyuozcrhw vt plaintext = hello entire world ciphertext = mgffpvhpufn Right now we have one long phrase.
This may appear like a little success but what if we have got a word with a great deal of areas? Based on frequencies, we can presume where the room can be and have one limb in the door. Still, we expanded our potential keys by adding a room so what if we developed a very much larger space with uppercase characters, lowercase words, numbers, and particular characters?
Nicely by carrying out that we have got actually increased our essential room from 26! This makes an assault take more period and enables us to hidden our information even even more. I will admit nevertheless, the replacement cipher nevertheless isn't unsoIvable. In the same sense as just before, all the strike provides to do is use term frequencies to make reasonable guesses to the key. Still, let's play with this. I composed a python software to display how we could perform this in code.